Information Security Management Policy
1. Information Security Risk Management Framework
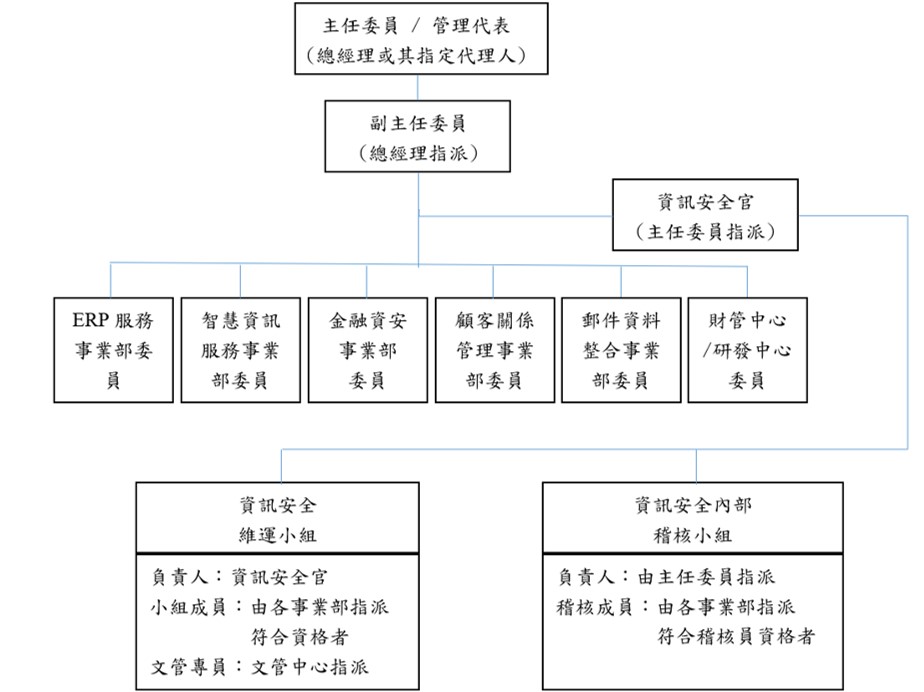
The company has established an Information Security Committee to effectively promote the information security management system, guiding the company's direction in information security development and demonstrating support from the management level. The Information Security Committee includes: the Information Security Operations Team, the Information Security Audit Team, and the Personal Data Protection Management Execution Team. They review relevant management systems and audit execution at least once a year, reporting on the performance of information security management to top management.
Organization Structure of the Information Security Committee
2. Information Security Governance System
To maintain the sustainable operation of the company's business and strengthen the information security management system, ISO 27001 Information Security Management International Certification was obtained in 2009. Annual verification reviews are conducted by a fair third-party verification agency to ensure the confidentiality, integrity, and availability requirements of information assets, enhance the reliability of information processing facilities and network systems, and increase employees' awareness of information security, effectively and reasonably reducing enterprise operational risks.
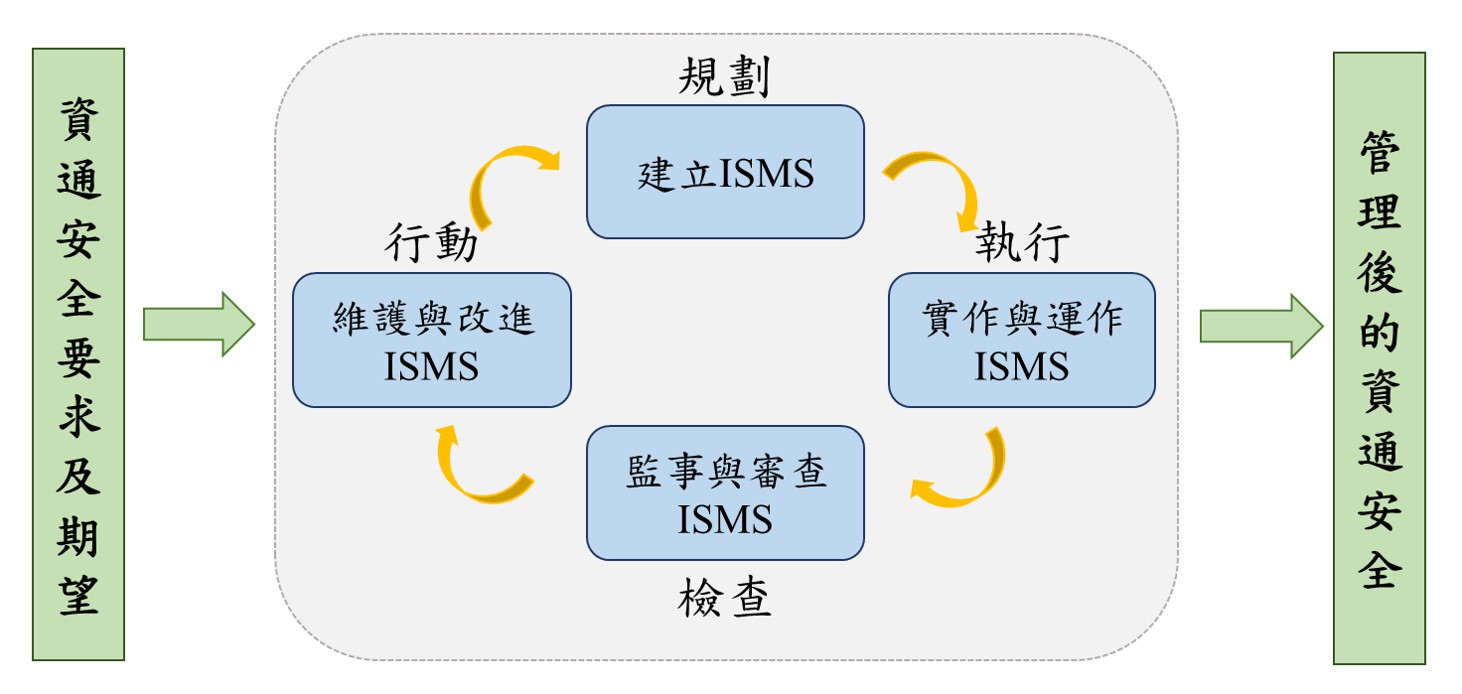
3. Specific Management Plans
To avoid incidents such as improper use, leakage, tampering, or destruction of information due to human error, intentional acts, or natural disasters, which may pose risks and harm to the company, specific management measures are as follows:
(1) Network Security: Continuously update protective equipment, firewall settings, intrusion defense settings, and webpage reputation evaluations. Implement network detection applications for record management. Email services include virus scanning and spam blocking.
(2) Device Security: Install antivirus software on each terminal device to block malicious virus intrusions in real-time. For remote office needs, implement SSL VPN tools to enhance the security of remote work.
(3) System Management: Computer systems should have sufficient permission management. Access control management procedures should set permissions for new employees or permission changes. Immediate locking, suspension, or removal of accounts and permissions should be conducted for departing employees according to procedures to prevent unauthorized use.
(4) Supply Chain Information Security: Suppliers must comply with the company's information security policies and related regulations and perform confidentiality operations according to contract requirements and mutual agreements.
(5) Data Security Protection: Establish data backup mechanisms according to backup and recovery management procedures. Backup operations should be performed daily, weekly, and monthly based on data attributes, and regular disaster recovery drills should be conducted.
(6) Education, Training, and Promotion: Newly recruited employees must complete information security education and training courses. Additionally, online education, training, and promotion are conducted annually for all employees to enhance their awareness of information security.
4. Major Information Security Incidents
No major information security incidents occurred in the company in the 112th fiscal year. However, with new attack methods constantly emerging, the company faces ever-changing and increasing information security threats. The company must continue to improve information security management to reduce operational risks and provide shareholders with the greatest investment value and benefits.
5. Information Security Risks and Countermeasures
The company ensures the adequacy and effectiveness of information security regulations and procedures through continuous review and evaluation, but cannot guarantee that the company will not be affected by emerging risks and attacks. Network attacks may also attempt to steal the company's trade secrets and other confidential information, such as proprietary information of customers or other stakeholders, and personal information of company employees. Specific countermeasures are as follows:
(1) Information Security Management Operation: The company's information security organization consists of various business units, with business unit managers serving as members of the information security organization. Each member is assigned personnel from their respective business units to serve in the information security maintenance team and the information security audit team, totaling 48 people. The Information Security Operations Team and the Information Security Audit Team held two reviews of relevant management systems and audit execution in the 112th fiscal year and reported the performance of information security management to top management. No deficiencies were found during the third-party verification audit conducted in October 112.
(2) Optimization of Defense-in-Depth Information Security Architecture: Continuously sign Trend Micro antivirus licenses to build computer-type endpoint antivirus measures, strengthen network firewalls, combat ransomware intrusions, introduce advanced information security equipment such as DLP solutions to prevent data leaks, and implement APT internal threat detection systems to prevent destructive software. This aims to prevent the company from suffering malicious attacks or extortion, as such attacks may result in delays or interruptions in business operations and require compensation for customer losses. In the 112th fiscal year, the company invested NT$1.4 million in optimizing the defense-in-depth information security architecture.
(3) Education and Training: Conduct comprehensive information security education and training for all employees to enhance information security awareness, ensuring that information security operations are implemented throughout the organization with the support of senior management and various departments. Training methods:
- Provide 1-hour physical/online training courses for new employees, with 30 people passing the exam.
- Provide online training materials for employees to study independently and complete online exams, with 280 people.
